Nginx上使用Let’s Encrypt加密(HTTPS)&自动续期 官网
获取证书生成工具 certbot 1 2 wget https://dl.eff.org/certbot-auto chmod a+x certbot-auto
获取证书 1 ./certbot-auto certonly -d *.域名 --manual --preferred-challenges dns --server https://acme-v02.api.letsencrypt.org/directory
按照提示依次填写邮箱地址,同意服务条款,绑定IP就行了。
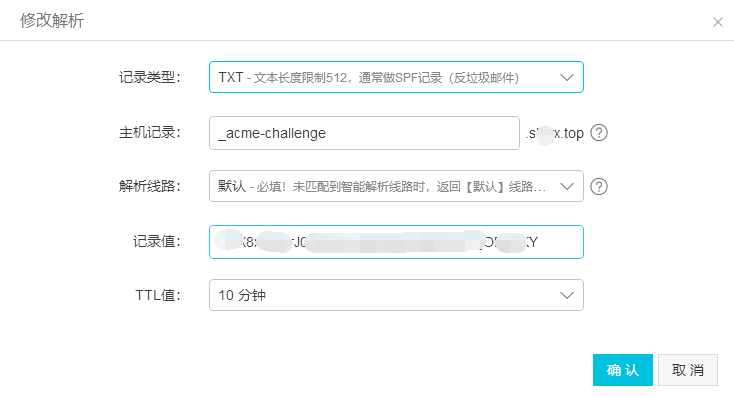
面这一步很关键,需要你配置你的域名TXT记录,以校验域名所有权,也就是判断证书申请者是不是该域名的拥有者。
1 2 3 4 5 6 7 8 Please deploy a DNS TXT record under the name _acme-challenge.shiyx.top with the following value: l1VX8xfEnhrJ02QB4o-M6ntb9JEsItRISb1YjOEw3KY Before continuing, verify the record is deployed. ------------------------------------------------------------------------------- Press Enter to Continue
在添加txt记录到你的域名之前,切勿点击回车键。
登陆域名解析控制台(阿里云),添加一条TXT记录:
执行命令:dig -t txt _acme-challenge.shiyx.top
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ubuntu@ip-172-31-16-20:~$ dig -t txt _acme-challenge.shiyx.top ; <<>> DiG 9.10.3-P4-Ubuntu <<>> -t txt _acme-challenge.shiyx.top ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 54437 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;_acme-challenge.shiyx.top. IN TXT ;; ANSWER SECTION: _acme-challenge.shiyx.top. 60 IN TXT "l1VX8xfSnwrJ02QB4o-M6ntb9JEsItRISb1YjOEw3YY" ;; Query time: 2001 msec ;; SERVER: 172.31.0.2#53(172.31.0.2) ;; WHEN: Thu Apr 26 00:50:34 UTC 2018 ;; MSG SIZE rcvd: 110
确认生效后,按回车键继续
1 2 3 4 5 6 7 8 9 10 11 12 13 IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/shiyx.top/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/shiyx.top/privkey.pem Your cert will expire on 2018-07-24. To obtain a new or tweaked version of this certificate in the future, simply run certbot-auto again. To non-interactively renew *all* of your certificates, run "certbot-auto renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
证书申请完毕!证书和密钥保存在“/etc/letsencrypt/archive/”目录下
1 2 3 4 5 6 7 8 9 ubuntu@ip-172-31-16-20:~$ sudo tree /etc/letsencrypt/archive /etc/letsencrypt/archive └── shiyx.top ├── cert1.pem ├── chain1.pem ├── fullchain1.pem └── privkey1.pem 1 directory, 4 files
续期HTTPS证书 官网:
https://certbot.eff.org/docs/using.html?highlight=renew#renewing-certificates
续期HTTPS证书命令 自动续签HTTPS证书 Let’s Encrypt 证书的有效期只有 90 天,因此我们需要定期的对他进行续签,我们使用linux自带的cron来设定计划任务
注意,如果你是第一次运行 crontab 命令,它会问题使用哪一个编辑器,你可以根据自己的需要进行选择,我选择的是 vim-basic
添加配置:
1 30 2 * * 1 sudo certbot renew
上面的执行时间为:每周一半夜2点30分执行renew任务。
你可以在命令行执行sudo renew看看是否执行正常。
Nginx配置 官网:http://nginx.org/en/docs/
注:aws需要定义安全组,允许https入站规则
Webroot配置模式 Webroot 的工作插件放置在一个特殊的文件/.well-known目录文档根目录下,它可以打开(通过Web服务器)内由让我们的加密服务进行验证。 根据配置的不同,你可能需要明确允许访问/.well-known目录。
为了确保该目录可供Let’s Encrypt进行验证,让我们快速更改我们的Nginx配置。编辑sudo vim /etc/nginx/sites-available/default文件,并将下面代码添加进去:
1 2 3 location ~ /.well-known { allow all; }
1 2 3 4 5 sudo nginx -t -c /etc/nginx/nginx.confsudo service nginx reload
Nginx配置:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 server { listen 80 ; server_name www.shiyx.top; return 301 https://www.shiyx.top$request_uri ; server_tokens off ; } server { listen 443 ssl http2; ssl on ; server_name www.shiyx.top; if ($host != 'www.shiyx.top' ){ rewrite ^/(.*)$ https://www.shiyx.top/$1 permanent ; } ssl_certificate /etc/letsencrypt/live/shiyx.top/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/shiyx.top/privkey.pem; server_tokens off ; ssl_session_cache shared:SSL:1m ; ssl_session_timeout 5m ; ssl_protocols SSLv3 TLSv1 TLSv1.1 TLSv1.2 ; ssl_ciphers HIGH:!aNULL:!MD5; ssl_prefer_server_ciphers on ; location / { root html; index index.html index.htm; } location ~ /.well-known { allow all; } }
另附https检查网站
hhttps://www.ssllabs.com/ssltest/analyze.html
参考:
https://www.lao-wang.com/?p=142
https://blog.guorenxi.com/43.html
https://segmentfault.com/a/1190000005797776
http://www.cnblogs.com/stulzq/p/8628163.html
https://www.appinn.com/use-letsencrypt-with-nginx/
https://www.cnblogs.com/lzpong/p/6433189.html